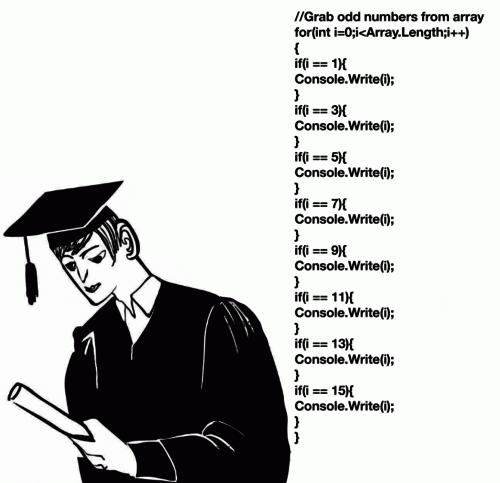
saw a 2nd year CS guy run a maze solver (for final exam) with 300 nested if-statements. worked about 50% of the time. so he added another 5000 nested ifs and got it up to 90%. good enough!
“CS Major” is one of my favourite memes
In my first CS class, the professor announced an extra credit project due at the end of the semester. It was to create a formatted terminal calendar given a year from user input. I finished it after learning about condition but before I learned about classes… or functions… or loops… or searching the internet… partially. I searched how leap years worked, but didn’t bother to search for code (Stack Overflow didn’t exist yet)
Anyway, long ass program with each month hard-coded with 7 possible calendars for each month depending on the first day of the week. Lots of copy and paste. Professor was speechless, but accepted it.
“It’s not stupid if it works”
300 nested if statements, (…) added another 5000 nested if statements.
At this point I want to doubt that they actually wrote it themselves, vs writing a metaprogram to generate the code.
One of the first real programs I wrote was a program to display telemetry data from a CAN bus. I was on the solar car team at uni, and we wanted to be able to view the data from the various systems live during the race. The CAN network was connected to a CAN-ethernet converter, which sent UDP packets over a wireless ethernet link to our lead car. I had no experience with networking, or UDP or CAN at all, but I had some documentation and a lot of free time, so I got to work.
Each device on the CAN network had a bit mask to identify it. For example, the bit mask for the motor controller might have been
0x1200. This meant that any packet starting with0x12belonged to the motor controller. For example,0x1201was one type of message, and0x1202another type, but both belonged to the motor controller.There was specific logic for each device on the network, so you needed to first figure out which device owned a packet using the bit mask, then apply the relevant logic to decode the packet.
Looking back, I realise the correct way to approach this would be to have a list of bit masks:
0x1200 0x1300 0x1400Then simply bitwise & any incoming packet with
0xff00, and lookup the result in the list of bit masks.Not knowing better however, what I actually did was create a giant dictionary of every possible packet value, so I could lookup any packet and determine which system it came from. This was so repetitive that I had to make use of my newfound super-power – vim macros – to complete the 8000 line dictionary…
Excerpt from real code below:
{ 0x102: { 'name': 'SHUNT_CMU_STATUS_TEMPERATURE_AND_VOLTAGE_1_2', 'data': [ 'cell_0_voltage', 'cell_1_voltage', 'cell_2_voltage', 'cell_3_voltage', ], 'unpack_string': 'intle:16, intle:16, intle:16, intle:16' }, 0x103: { 'name': 'SHUNT_CMU_STATUS_TEMPERATURE_AND_VOLTAGE_1_3', 'data': [ 'cell_4_voltage', 'cell_5_voltage', 'cell_6_voltage', 'cell_7_voltage', ], 'unpack_string': 'intle:16, intle:16, intle:16, intle:16' }, }


